Quality controls in Azure DevOps with Prisma Cloud
Azure DevOps Prisma Cloud
Table of contents:
This time I want to focus on quality by implementing CVE and compliance scan tool as well as the control gate on a release stage in Azure DevOps leveraging Prisma Cloud platform by Palo Alto Networks.
All code from this article is here
1├── README.md
2├── binaries
3│ └── twistcli
4├── pipelines
5│ └── azure-pipelines.yml
6└── src
7 └── Dockerfile
I would like to build my code using Azure DevOps pipelines and fail earlier as possible in case:
- of (whatever severity) vulnerabilities or failed compliance checks for built image;
- do not allow release in case of failed quality gates.
Also I’d like to get instant feedback about the issues so I can go ahead and fix it quickly.
For automated image scanning I am going to use Prisma Cloud.
Application #
I am going to use the following Dockerfile as it should bring me bunch of CVEs and highlight failed cheks againts Center for Internet Security (CIS) benchmarks and other compliance standards.
FROM vulnerables/web-dvwa
Prisma Cloud #
There are several things that I need to do in Prisma Cloud:
- Get console’s URL and store it’s string as variable or secret in Azure Key Vault;
- Generate and store (i.e. in Azure Key Vault) access and secret key so I can curl or CLI endpoints of Prisma Cloud;
- Download binaries of
twistcli(tool to do scans) and store it in Azure Artifacts as universal package in feed.
Alternatively I could use plugin for #3 and store #2’s credentials as service connection in AzDo, but the moment I wrote this article I had several issues with the plugin and looks like it does not get much attention either (also plugin is just a wrapper around twistcli).
Pipeline definition #
1pool:
2 vmImage: ubuntu-latest
3
4stages:
5
6
7- stage: BUILD
8 jobs:
9 - job: BUILD_AND_SCAN_CONTAINER_IMAGE
10 steps:
11
12 - task: Bash@3
13 inputs:
14 targetType: 'inline'
15 script: |
16 docker build -t myapp:$(build.buildid) .
17 echo "##vso[task.setvariable variable=imagesha;isOutput=true]$(docker images --no-trunc --quiet myapp)"
18 echo ${{ variables.imagesha }}
19
20 - task: UniversalPackages@0
21 inputs:
22 command: 'download'
23 downloadDirectory: '$(System.DefaultWorkingDirectory)'
24 feedsToUse: 'internal'
25 vstsFeed: 'e19a49e7-5eae-4186-ab59-41190cb528e2'
26 vstsFeedPackage: '5eac8bc8-e21a-473a-844c-97d9a0f71e3f'
27 vstsPackageVersion: '0.0.2108525'
28
29 - task: Bash@3
30 inputs:
31 targetType: 'inline'
32 script: |
33 chmod +x twistcli
34 ./twistcli images scan --details --address $CONSOLE -u $ACCESS_KEY -p $SECRET_KEY myapp:$(build.buildid)
35
36- stage: DEV
37 jobs:
38 - deployment: DEV
39 environment: dev
40 strategy:
41 runOnce:
42 deploy:
43 steps:
44 - script: echo push
Environments, approvals and checks #
For the quality gates I am going to call Prisma Cloud’s endpoint to check my image for any issues (this is done via environment’s approvals and checks by invoking REST API). The following screenshots show both service connection for the endpoint (with it’s credentials) and the success criteria. In order to keep it simple image’s sha is being passed as plain text in URL as well as simple success criteria is being validated (either anything being returned with false boolean in pass argument). API’s references for scan results.
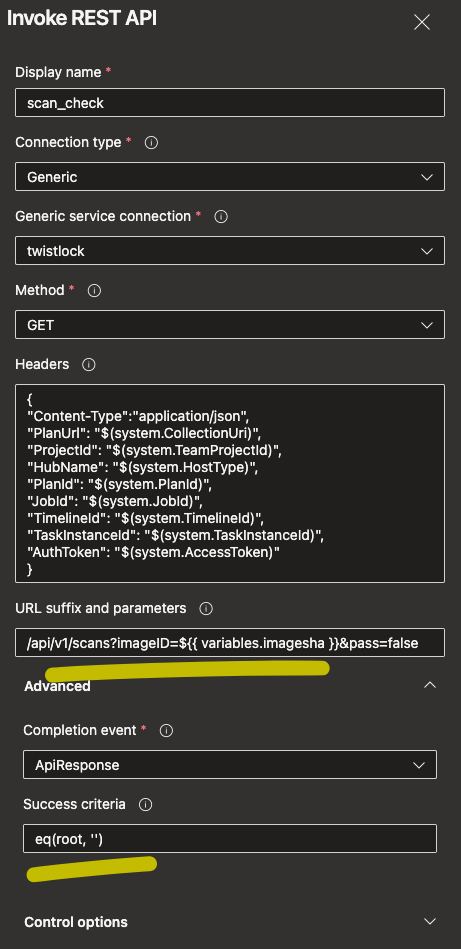 {: .normal }
{: .normal }
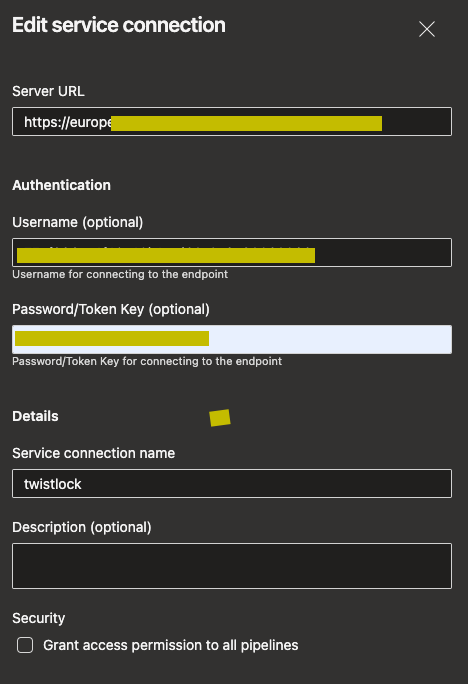 {: .normal }
{: .normal }
Flow #
- Developer submits the code and raises PR.
- Pipeline starts to run two stages;
- BUILD stages uses docker build command to build the image, tag it and get the SHA of the image; following by further built image is being scanned by twistcli utility (it’s binary is being downloaded from the feed as universal package to the agent); CVE and compliance alert/failure severities can be controlled via Prisma Cloud’s UI (i.e. I can fail build if any low/medium CVE are found during scan with immediate feedback in the logs of Azure DevOps Pipeline);
- DEV stage has a references to
devenvironment that contains approval and checks. Check submits payload with image’s SHA and checks whether it has any CVEs and compliance issues (and if yes fails the stage).
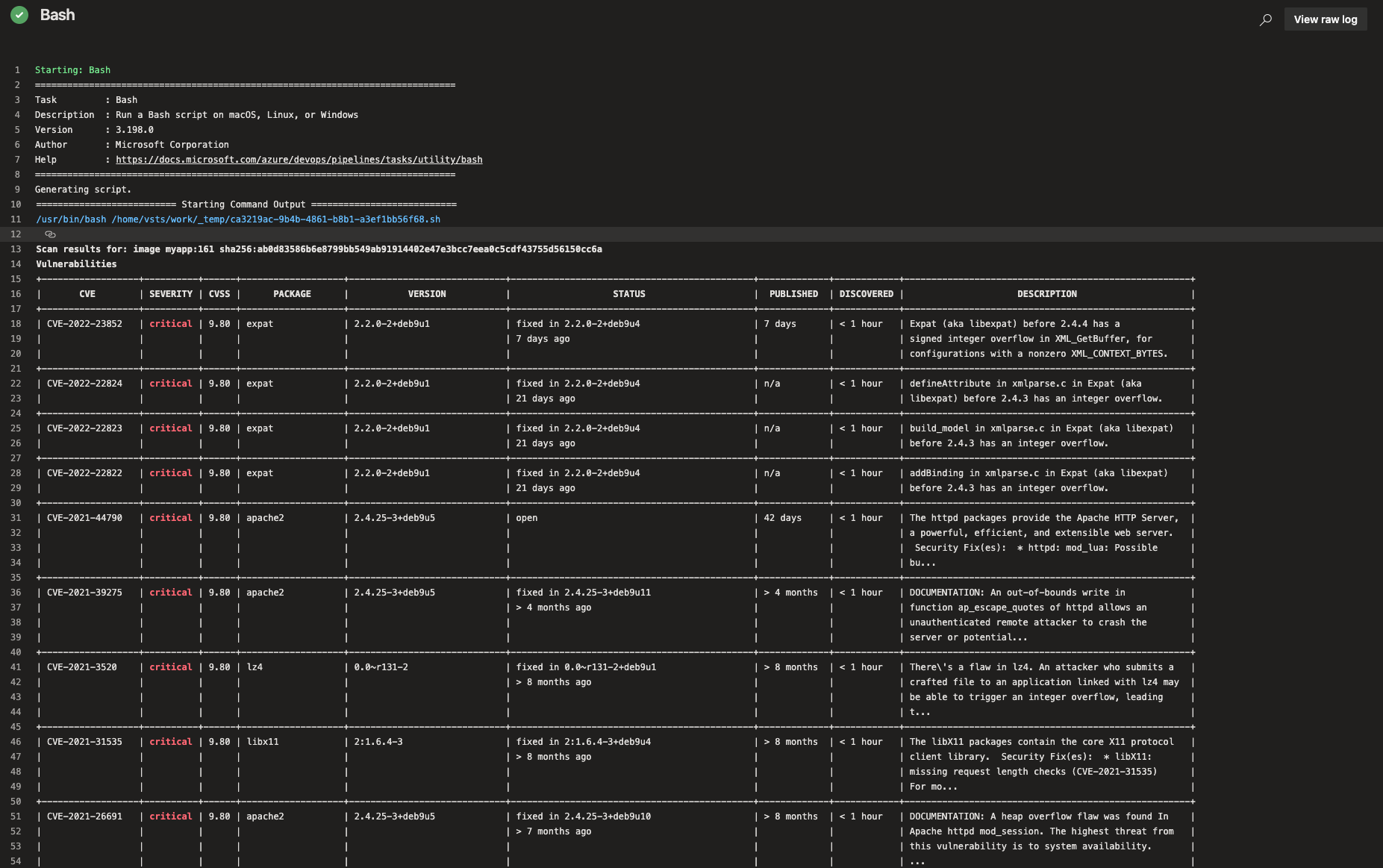
That’s it! I have build stage with image scan task and a quality gate that automatically fails my deployment stage in case of any vulnerabilities or compliance issues.